FreeBSD Wifi on a BCM4328 Wireless Card
Overview
Notes about configuring a wifi wireless network on FreeBSD 12.1, using an old laptop with an unsupported wireless card. Lots of forums said that the card is not supported and that it could not be done. But I refused to believe it, and this is a testimony to the resilience of FreeBSD.
-
OS: FreeBSD 12.1-RELEASE-p10
Laptop: Dell Inspiron 1525 (circa 2007)
Memory: 4GB
Wireless Card: 802.11g Broadcom BCM4328 SIBA bus BCM4312 rev 15
The history: while running FreeBSD 12.1 everything worked on my old Dell Inspiron 1525 laptop, except my wifi network. Going through blogs I discovered that the wifi card is not supported by generic FreeBSD kernel, so it does not work by default; and requires special tweaking. There’s no official guide for this wireless card. Tried many different recommendations from forum postings. Below is what what worked for me. There may be better ways; but if so then please comment.
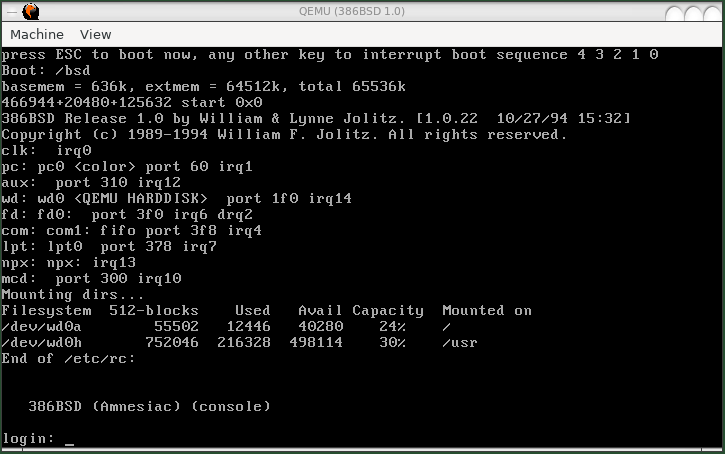
386BSD 1.0 Running on Qemu
DICLAIMER: This software is a component of “386BSD” developed by William F. Jolitz, TeleMuse.
Please review the full COPYRIGHT NOTICE before continuing.
With Qemu I was able to install and run 386BSD 1.0 Jolix (circa 1989-1994). It is not for the faint of heart. The public downloaded zip file came with no floppies, no CDROM, no installer; only the OS binaries. I had to figure out many things by trial and error, rinse and repeate: the best hard drive image format, dumping the OS binaries remotely, labeling the bootstrap, and fine tuning the startup procedures. Many undocumented steps were involved. I will possibly work on the step-by-step instructions once I am able to re-compile and figure out a stable running install.
386BSD is a historical and legendary operating system, because it is the first Unix that was ported to the Intel 386 CPU beginning in 1989. This preliminary version paved the way for all the other popular Unix versions in actuality, including FreeBSD, NetBSD and the like. This release, together with Minix, is part of the foundations of the modern Unix and Linux for the 386; it is a great academic point of reference for operating system porting and development today, especially for the x86 personal computer architecture; and TCP/IP networking, which also originated with the earlier 4.2BSD Unix.
Unix BSD/OS 4.3 Install on Qemu 386
Overview
A practical approach for the Qemu 386 install of the operating system from Berkeley Software Design BSD/OS 4.3 (2002). Installing and running a legacy Unix system is a great point of reference concerning the study and appreciation of older operating systems. BSD/OS 3.x to 5.x also install in a very similar way. The audience is experienced Unix and Linux administrators.
CLARIFICATION: This is the BSD/OS 4.3 version for i386 from 2002, and not the classic 4.3BSD Berkeley Unix for the VAX from 1986. For that install visit Install 4.3BSD Berkeley UNIX with VAX780 SimH Emulator and TCP/IP Networking
COPYRIGHT
The copyright declaration as seen inside the mounted ISO download:
$ cat COPYRGHT BSD/OS Release 4.3 Copyright 2001 Wind River Systems, Inc. Copyright 1992,1993,1994,1995,1996,1997,1998,1999,2000,2001 Berkeley Software Design, Inc. Portions Copyright by other entities, see individual modules for details. Use of this software is governed by the Wind River Systems, Inc. Software License. If you do not accept the terms of this license, immediately return the distribution to the place of purchase for a full refund. Further use of the software will be considered to be acceptance of the terms of the license.
Download
Download 4.3BSD [612MB]: https://archive.org/download/bsdos-4.3/bsdos-4.3-binary.iso
$ mkidr -p /u1/qemu/4.3bsd $ cd /u1/qemu/4.3bsd $ wget https://archive.org/download/bsdos-4.3/bsdos-4.3-binary.iso